· Vulnerability: weakness in an organisation's assets that when exploited by a threat will lead to economic loss.
· ISO27005 Information Security Risk Management in the following areas:
Organization
Processes and procedures
Management routines
Personnel
Physical environment
Information system configuration
Hardware, software or communications equipment Dependence on external parties
Vulnerability Reporting
· When a vulnerability is discovered, it is usually reported to the organisation responsible for the product and they are given time to fix.
· Zero Day vulnerability is one that is unknown (or unfixed) by the manufacturer of the product when it is exploited.
· Vulnerabilities that are reported and then fixed, by a patch or upgrade of the software or product, is then reported for inclusion in public databases:
CVE Common Vulnerabilities and Exposures (https://cve.mitre.org/index.html)
NVD National Vulnerability Database (https://nvd.nist.gov/)
VulDB (https://vuldb.com/)
· Disclosure comes with problems because it may help disseminate and promote exploits.
· There is a market for bug finding (Bug Bounties) and also for selling Zero Days.
Vulnerability Scoring
· Vulnerability scoring measures (NVD):
Attack vector: network, local, physical.
Privileges required: None, low, high.
User interaction: None, required.
Impact on CIA: None, low, high.
· CWSS: more complex and based on 3 measures:
Base Findings: captures the inherent risk of the weakness, confidence in the accuracy of the finding, and strength of controls.
Attack Surface: the barriers that an attacker must overcome in order to exploit the weakness.
Environmental: characteristics of the weakness that are specific to a particular environment or operational context.
Exploits and Proofs of Concept
· Vulnerabilities are not really risks unless they are exploitable. In part, proving a vulnerability relies on showing how it can be exploited.
· Researchers often develop a proof of concept: a working way of exploiting a vulnerability.
· There are databases of known exploits to vulnerabilities: SearchSploit (and others) https://www.exploit-db.com/searchsploit
Vulnerability Sharing
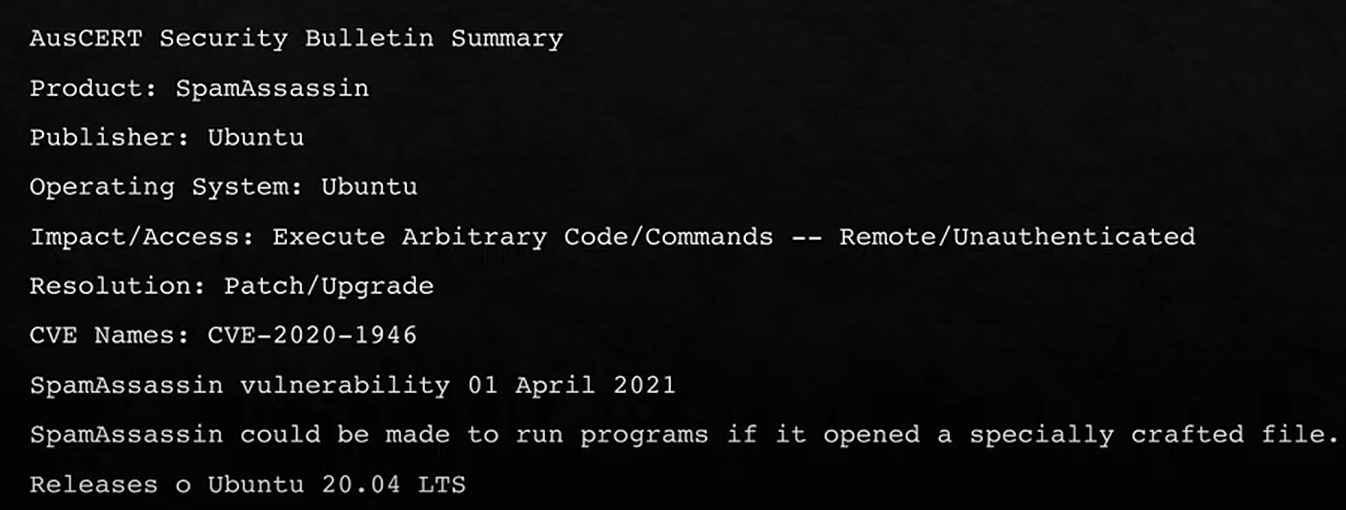
· Countries have Computer Emergency Response Teams (CERTs), but this term was trade marked by Carnegie Mellon University who started the first one in 1988.
· AusCERT is Australia’s but all countries have their own.
· Responsible for alerting organisations about specific vulnerabilities and threats.
· Example:
Network Vulnerabilities and Attacks
· Vulnerabilities that directly involve networks and their protocols:
Network traffic is vulnerable to interception, being read and manipulated.
Network services are vulnerable to poor availability by being overloaded.
· Sniffing: listening to traffic on a wired or wireless network (WiFi, Bluetooth, NFC).
May involve a "man-in-the-middle" attack.
Wireless can be passively sniffed because it is broadcast.
· Spoofing: altering communications to pretend to be a different sender.
e.g. Caller ID on an SMS or phone call, senders of emails.
Usually done at the network level altering TCP/IP packets.
Part of a man-in-the-middle attack.
· Denial of service: Flooding a service with fake requests so that real users can not access the service.
· Distributed Denial of Service (DDoS): Using many sources for denial of service attacks including Internet of Things (IoT) devices.
· Man-in-the-middle attacks: Intercept network traffic to sniff the packets before passing them to the legitimate destination or to a destination under the attacker's control.
· Hacking: Initial Access and Lateral Movement
Access a machine through the use of remote access services or through exploitation of vulnerabilities in a network service.
Use a machine to “pivot” to other machines on the same, or different networks.
Web Vulnerabilities
· Some of the most common applications we use are web applications that are run by web servers. Examples include: Banking website, Netflix, Amazon.
· They communicate with browsers and send code and media to display.
· Some functionality is run on the browser, but important things like “transfer this money to my friend” are done on the server.
· There are numerous places where vulnerabilities can exist and there are common ones that occur.
· OWASP Top 10 (Open Web Application Security project maintains top 10 vulnerabilities):
Programming errors
Authentication
Input sanitization: injection, cross-site scripting (XSS)
Security and acess
Configuration errors
Insufficient logging or monitoring
Security configuration
3rd Party programming errors
Using components with known vulnerabilities.
Finding Vulnerabilities: Scanning
· Use tools that carry out an automated scan of the network and its services:
nmap
OpenVAS
BurpSuite
Nessus
· These will look for vulnerabilities based on a database. They rely on being able to version software discovered accurately to be able to check if there are known vulnerabilities. i.e. it doesn’t try and exploit vulnerabilities.
Finding Vulnerabilities: Penetration Testing (渗透测试)
· Penetration Testing (Ethical Hacking)
Professionals who use tools and their skills to look for vulnerabilities.
Will operate within an agreed scope regarding what they can and can't do.
May be done as White Box, Grey Box or Black Box depending on how much information is provided about the network and the applications that are running on them.
· Red Teams
Teams of ethical hackers that will try and penetrate a network, sometimes adopting Tactics, Techniques and Procedures of known hacker groups.
They may operate against a Blue Team that tries to defend against the attack.
The purpose again is to highlight vulnerabilities.
Sometimes Blue and Red teams are combined to form Purple teams.
Implementing Controls
· Implement Defense in Depth: i.e. have multiple layers of controls that implement security at each level.
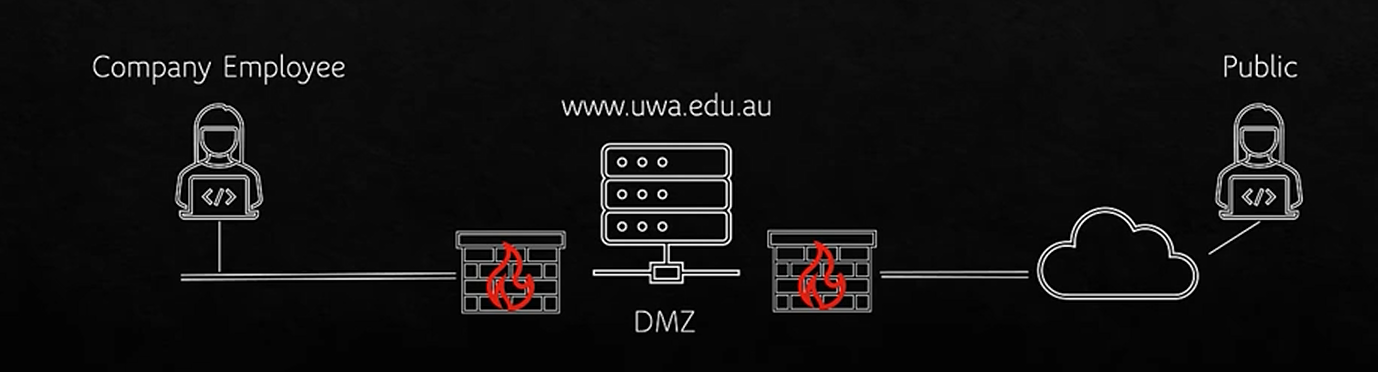
· Traditionally, people implemented a perimeter firewall to protect company, This doesn’t work so well when everyone is working remotely.
· Partition the network into different functional concerns e.g. Departments in an organisation, servers from the administration network, staff from students.
· Externally facing services like web servers put into a DMZ (Demilitarized Zone).
Computers
· Computers are built up using a secure baseline image: configuration of Windows (for example) that has default user, system and security settings, certain software profiles.
· Can implement Australian Signals Directorate (ASD) Essential Eight:

Application Control
· Vunlerabilities:
Windows has a variety of scripting languages that can be used for malicious purposes.
They can be run from the command line applications cmd.exe, powershell.exe and applications such as Microsoft Office (Word, Excel, PowerPoint) which runs VBScript and JScript (a form of JavaScript).
Although many attacks require a person to click on a link and allow a program or script to run, some do not need this.
· Controls
General users should be prevented from running scripts in PowerShell and another scripting environment Windows Script Host (WSH).
Launching applications on Windows (anything with a file extension of .exe) can be checked against a AllowList and BlockList.
· Microsoft Office Macros (宏)
Vulnerability
Office has the ability to automate actions by running a Macro which is a piece of script that is labelled and associated with a key combination or some action such as opening a document.
Malicious users can craft macros that steal information (C) or run malware (C, I, A).
Controls
Microsoft has made it harder to run macros because you need to agree to running them but that is not too hard with some users.
Block macros in Office and train users.
Restrict Administration Privileges
· A user with administrator privileges can normally carry out all actions on a computer including installing programs and device drivers (software for printers, peripheral devices), managing user accounts, managing logging and auditing functions.
· On Linux and Windows there are special users root and Administrator but on consumer products main user is usually an administrator as well.
· Windows will now make explicit when a user needs to use administrative privileges.
· Vulnerability
Users are given administrator privileges when they don’t need these privileges for everyday use.
Attackers who get access to these accounts then have increased access thanks to the privileges (C,I,A).
· Controls
Limit the number of users who have administrator rights.
Train users to use them judiciously.
Monitor actions of anyone who uses these privileges.
Multi-Factor Authentication
· Normal authentication uses a single factor: a password (often referred to as “something you know” authentication type).
· Factors sometimes defined as:
Type 1: Something you know.
Type 2: Something you have.
Type 3: Something you are or something you do.
Somewhere you are.
Context-Aware Authentication.
· Vulnerability: Attacker obtains username and password and uses it to gain unauthorised access (C - possibly I, A).
· Controls:
Multi-factor authentication makes it harder for attacker to use a username and password.
However, some second factors like SMS codes are relatively easy to get around.
Daily Backups
· Vulnerability
Access to files and information stored on a disk because of: Disk failure, Lost device, Ransomware or deletion.
· Control: Daily backup, Cloud Storage.
· Issues
Problems with how frequently you backup.
Overheads of backups: storage, network use.
Time to restore.
Backup confidentiality, integrity and availability.
Patching Applications and Operating System
· A patch is a small update to application and operating system software that usually fixes bugs rather than introduces major features (referred to as an upgrade).
· Vulnerability
Known vulnerabilities in software can be exploited by attackers.
Issuing a patch tells attackers about vulnerabilities.
· Control: Update applications and operating system with patches as soon as they are available.
· Issues
Patches are often complicated and can impact the availability of systems themselves.
Issuing a patch informs attackers about vulnerabilities and increases the attacks.
User fatigue in constantly updating their systems.
Application Hardening
· Vulnerability
Many applications come with features and default settings that are insecure.
Default passwords that are the same for each product.
Examples are IoT devices, Routers, server software.
· Control
Harden application by removing default features and settings, setting new passwords.
Anti-Malware Software
· Anti-Malware software (AKA Anti-Virus) can be installed at endpoints (computers, mobile devices, tablets) or on edge devices like routers.
· Works in real-time scanning network traffic, scan file changes and can do disk scans.
· Works by looking for a range of indicators such as file signatures based on file hashes, presence of certain strings (text), use of system functionality that is not normal for applications.
· More recently anti-malware operates on behavioural analysis (anomaly-based): behaviour typical of malware, unexpected network traffic, attempts to change memory or other applications: This is increasingly done using machine learning techniques.
· Software also does other things now like looking for suspicious browsing, blocking websites that are known malware sites.
· Malware adapted and tries to evade (including anomaly-based software) and even disable anti-malware software.
Intrusion Detection Systems
· Intrusion detection system (IDS) can be network-based or host-based.
· Like anti-malware, uses knowledge-based and behavioural-based approaches to detection.
· Behavioural based approaches take a baseline of network traffic and other factors and looks for changes.
· IDS systems report back to a Security Information and Event Manager (SIEM) which can alert security staff of issues.
· IDS may take some active measure such as blocking traffic on finding an anomaly.
Intrusion Protection Systems
· Intrusion protection system (IPS) is usually placed inline in the network.
· Like IDS, uses knowledge-based and behavioural-based approaches to detection.
· IPS will take active measures to block malicious activity.
· Sometimes combined as IDPS.
· Open Source example Snort.
Honeypots

Data Loss Prevention (DLP)