Threats
· Threat is anything that can exploit a vulnerability in a way that leads to a negative impact.
· Threat actor could be a person, a group or external force responsible for threats.
Can be internal and external.
External actors can be environmental: earthquakes, fire, flood, wind, etc.
Internal actors may have motivation that is malicious or simply error.
· Threat Action: What the threat actor did or caused e.g. malware, hacking, social, etc.
Threat Reports
· When looking at data for attacks, consider who is reporting the data, how it was collected, what their motivations are.
Cybersecurity companies use analysis as a marketing tool to show how good they are.
Governments use analysis and blame as a geopolitical tool.
Apply Occam's Razor: if there are two competing hypotheses for a phenomenon, pick the simplest (the one with the fewest assumptions)
· We only find out about what is reported or observed, it is often only the tip of the submerged iceberg. (只会看到想让你看到的内容)
SEI’s Hybrid Threat Modelling Model
· Identify potential threat actors (Persona non grata, 不受欢迎的人)
Purpose: What is the actor’s motivation, goal or intent?
Target: What asset is the target?
Action: What action does the actor perform?
What Skills does the actor need?
What Resources does the actor need?
Result of the action: what goal has the actor achieved
Impact: severity of the attack
Threat type: (denial of service, spoofing...)
· We can build a threat model based on this example:
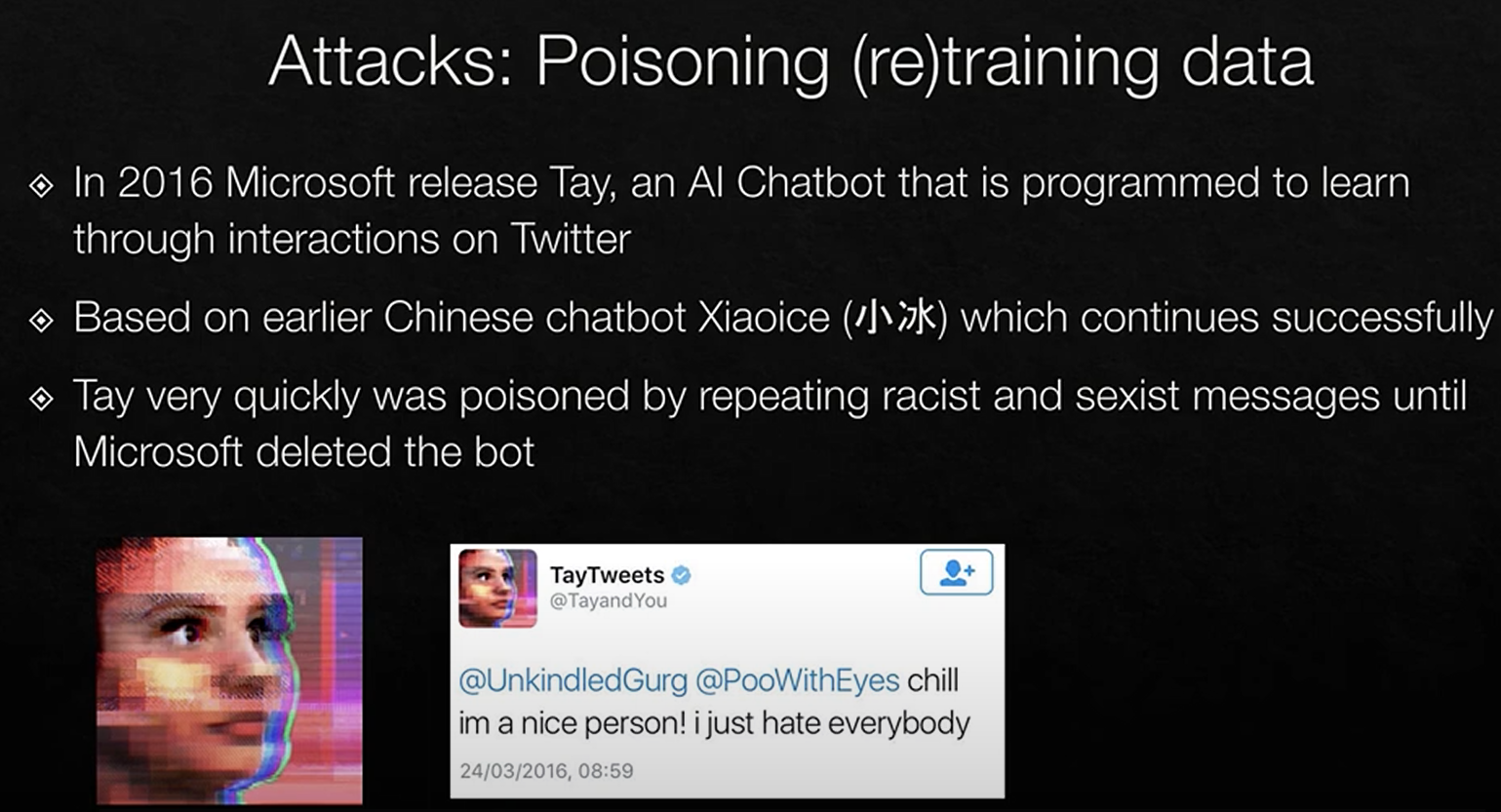
Threat actor: Malicious Twitter users
Purpose: To poison Tay's training to get the bot to say inappropriate things.
Target: The training of the chatbot network
Action: Repeated interactions by multiple users reinforcing inappropriate phrases.
Skills required: none
Resources needed: Twitter account
Result of the action: Tay chatbot makes inappropriate comments.
Impact: Tay is deleted as a service on Twitter, Microsoft is embarrassed.
Threat: Integrity, Availability
Incidents
· A cybersecurity event is any occurrence related to assets or the environment that indicate a possible compromise of policies or failures of controls, or something unmapped situation that could impact security.
· A cybersecurity incident is when one or more information security events compromise business operations and information security.
· A data breach is the actual unintentional release of secure or private/confidential information to unauthorized individuals or to an untrusted environment.
Threat Actions
· Stands for what a threat actor has done to cause or contribute to an incident.
Malware
Hacking
Social
Misuse
Physical
Error
Environmental
Malware
· Malware is any malicious software, script or code that is run on a device that alters its state or function without the owner’s informed consent.
Virus: malware that infects files and spreads when those files are copied to new hosts.
Remote Access Trojan: software that disguises itself as something normal or innocuous.
Spyware: software on mobile phones and PCs that performs keylogging, reading messages, emails, etc.
Worm: malware that propagates itself through the network.
Adware: usually browser based software that displays ads.
Scareware: malware that displays threatening messages to the user e.g. the police have been informed about your activities on the computer.
Bot: malware that is under the control of a command and control centre (C2) that can launch attacks such as sending spam or Denial of Service.
Ransomware: Encrypts folders and files and demands payment to unencrypt (usually payment is in cryptocurrency like monero).
Cryptominer: malware that uses computer resources to mine cryptocurrency.
· Examples:
2000 - ILOVEYOU: The ILOVEYOU worm used a social engineering trick that persists even today. It arrived as a spam email attachment, eventually infecting about 10% of all internet-connected Windows computers.
July 2001 - CodeRed: Named after the flavor of Mountain Dew its discoverers were drinking at the time, CodeRed used a buffer overflow vulnerability in IIS to spread itself and deface websites. It was followed a month later by an upgraded version that installed a backdoor on networked computers.
2008 - Conficker: Conficker rapidly infected millions of computers worldwide but did not result in much damage. We still don't know the worm's true purpose, but thousands of hosts remain infected to this day, and Conficker scan traffic routinely is detected as part of the internet's "background radiation."

2009 - Stuxnet: Stuxnet was one of the first digital weapons to target a physical system: Nuclear refinement centrifuges used by Iran to enrich uranium. Stuxnet's enduring legacy is that it permanently opened the door to nation-states' use of malware as a tool of war.
May 2017 - WannaCry: WannaCry, the most widespread ransomware-worm hybrid seen, demonstrated (again) how a lapse in patching can have dire consequences. It relied on exploits stolen from the NSA and publicly released by The Shadow Brokers. The attacks forced Microsoft to release out-of-band updates for unsupported products.
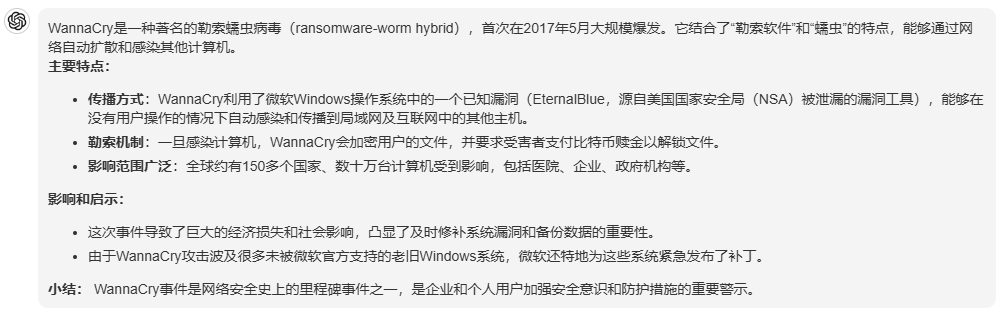
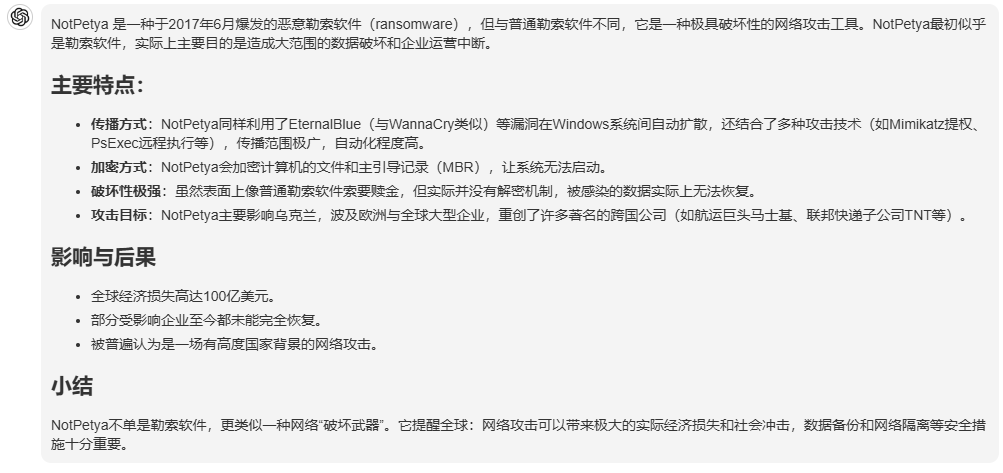
June 2017 - NotPetya: NotPetya crippled some of the world's largest shipping and logistics companies, reportedly causing over $10 billion in damages. Some of the affected companies have yet to fully recover.
Malware Evasion
· Malware can be detected by
Static analysis: checking signatures: the hash of the program or the presence of text (strings), code that only malware would use.
Dynamic or behaviour analysis.
· Malware usually tries to evade detection (and removal) using a variety of techniques.
Code Obfuscation:
Encryption
Polymorphism (多态性): encrypting (packing) but use different encryption and decryption techniques
Metamorphic (变质): change the actual code being used
Hacking
· All attempts to intentionally access or harm information assets without (or exceeding) authorization by circumventing(规避) or thwarting(阻挠) logical security mechanisms.
Examples of actions: Backdoor, Brute force, C2, DoS, Exploit Vulnerability, Network sniffing, SQL Injection
Cyber Kill Chain
· Originated from military analysis of an attack, developed by Lockheed Martin.
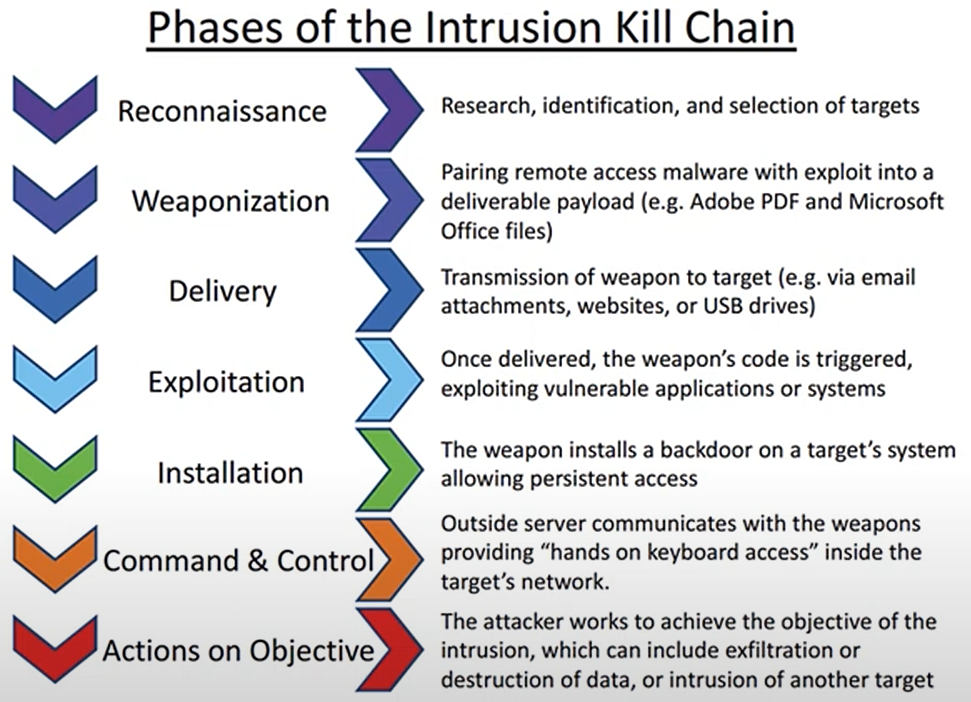
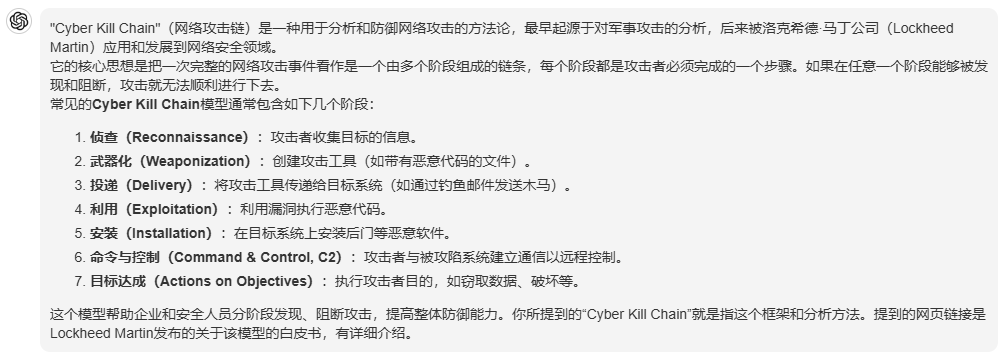
· MITRE ATT&CK: a comprehensive knowledge base that outlines the tactics, techniques, and procedures (TTPs) that adversaries may use during cyber attacks.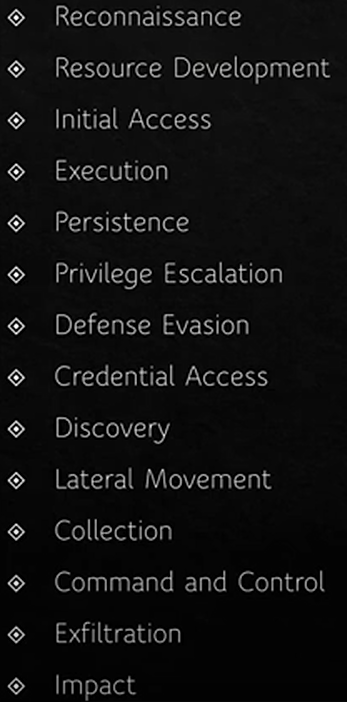
Social Engineering
· Social tactics employ deception(欺骗), manipulation(操控), intimidation(恐吓), etc to exploit the human element, or users, of information assets.
Baiting(诱饵): Baiting (planting infected media, USB etc)
Bribery(贿赂): Bribery or solicitation
Elicitation(引出): Elicitation (subtle extraction of info through conversation)
Extortion(敲诈勒索): Extortion or blackmail
Forgery(伪造): Forgery or counterfeiting(假冒) (fake hardware, software, documents, etc)
Influence: Influence tactics (Leveraging authority or obligation, framing, etc)
Scam: Online scam or hoax(骗局) (e.g., scareware, 419 scam, auction fraud)
Phishing(网络钓鱼): Phishing (or any type of *ishing),
Pretexting(借口): Pretexting (dialogue leveraging invented scenario)
Propaganda(宣传): Propaganda or disinformation
Spam(垃圾邮件/信息): Spam (unsolicited or undesired email and advertisements)
· This works because people:
want to be helpful
tend to trust people and communications that come from trusted people
are concerned about getting in trouble
are willing to cut corners(偷工减料)
are willing to believe in good fortune
don't understand how technology works
Phishing
· Sending emails, direct messages, SMS and other forms of communication pretending to be a trusted party and getting the target to click on a link to provide information or download malware.
· Relies on credible email and a credible phishing site to capture credentials etc.
· Spearphishing(欺诈式钓鱼): targeted email aimed at a specific victim. (量身定制的钓鱼)
· Business Email Compromise (BEC) specific phishing related to business.
· Whalephishing(鲸鱼钓鱼): Phishing a high value target such as a CEO.
· Phishing works on the basis of sending large number of emails so that even a small success rate will be a reasonable number of usernames and passwords.
