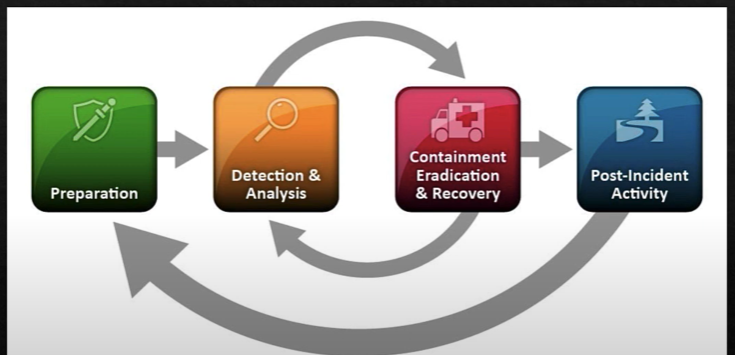
Definition of an Incident
Any event that has compromised confidentiality, integrity or availability of an organisation’s assets.
From a VERIS perspective, an incident is the result of an Actor, taking some Action, on an Asset, resulting in the Attributes of an incident, i.e., how it was affected. In this case, the action exploits a vulnerability in the asset.
An incident is when there is actual loss or imminent(adj.迫在眉睫的) threat of loss. Otherwise, it is an Event.
Standard for incident handling is NIST SP800-61, it defines an incident as: “A computer security incident is a violation or imminent threat of violation of computer security policies, acceptable use policies, or standard security practices”.
Handling an Incident:
Note about "Hack Back" (黑客反击):
In the process of investigation and remediation(补救), there may be the temptation to take direct action against hackers. This is known as “Hack back”.
Very few organisations or governments think this is a good idea (despite some enthusiasm from certain politicians in the US and UK).
There is no legal basis for it as hacking back may involve other countries, other infrastructure and innocent third parties.
It is not the role of a business to engage in cyber actions and this should be left to legal authorities.
Incident Response Team
Not all organisations can afford a dedicated incident response team.
A service offered by outside contractors as well as through cyberinsurance companies.
Need to have a variety of skills:
Technical: cybersecurity, programming, IT, networks, forensic(取证) cybersecurity.
Communications: liaising(联络) with senior staff in organisation and outside organisations.
Stressful environment on 24x7 call.
Can be involved in security awareness training and also information sharing with other companies and CIRTS/CSIRTS/ISACS
Have a Jump Bag with hardware and information needed for handling a response.
Incidents Detection
Incidents may come to light through alerts from:
IDPS (入侵检测与防御系统)
Anti-malware software
Users noting irregular behaviours on their computers or accounts
Breached data surfacing on the Dark Web or other criminal sites
Dwell time (潜伏时间): amount of time an attacker spent on a system before detection determined from:
Mean Time to Detect (MTTD, 平均检测时间) and Mean Time To Respond/Remediate (MTTR, 平均响应&修复时间)
Incidents: Detection and Analysis
During this phase, the team are trying to answer the question
Who?, What?, Where?, Why? and How?
Have to be careful since incidents may be the subject of criminal proceedings and so evidence needs to be collected to preserve chain-of-custody (证据链).
This requires special equipment that can be shown not to alter information, for example from a disk copy or during the examination of a computer
Incidents: Making detection and analysis easier
Detection is simpler if system and network operation procedures are set up in a way to facilitate this:
Understand normal behaviours
Have a log retention policy (日志保留策略)
Perform event correlation (事件关联分析)
Keeping all host clocks synchronized
Use packet sniffers (包嗅探) for additional data
Get help!
Incidents: Incident Reporting
The current status of the incident (new, in progress, forwarded for investigation, resolved, etc.)
A summary of the incident
Indicators related to the incident
Other incidents related to this incident
Actions taken by all incident handlers on this incident
Chain of custody, if applicable
Impact assessments related to the incident
Contact information for other involved parties (e.g., system owners, system administrators)
A list of evidence gathered during the incident investigation
Comments from incident handlers
Next steps to be taken (e.g., rebuild the host, upgrade an application)
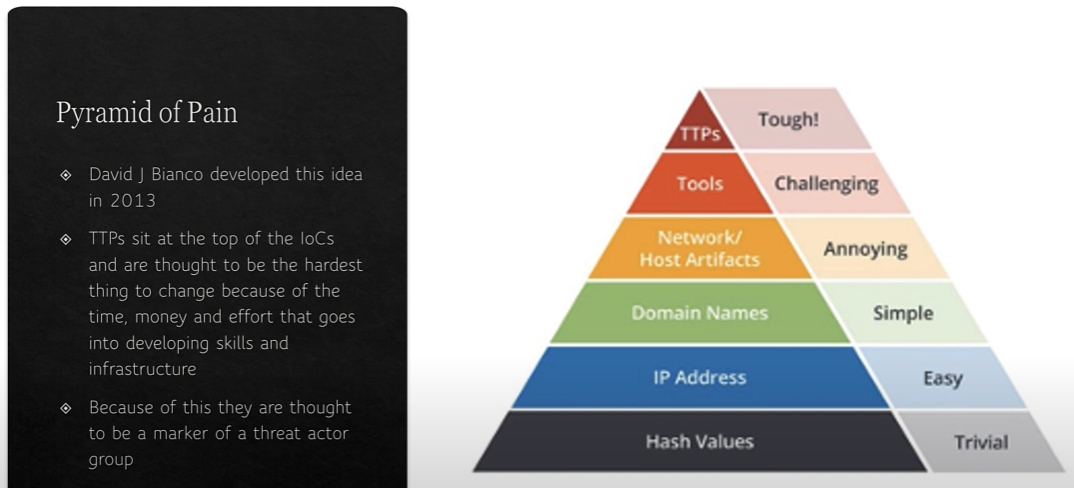
Indicators of Compromise (威胁指标)
Indicators of compromise (IOC) are pieces of forensic data (取证数据) that identify a malicious attack. They include:
Unusual (outbound) network traffic (异常出站流量)
Anomalies in privileged account behaviour (特权账户异常行为)
Geographical irregularities: logins from new locations and countries, network traffic from specific IP addresses (地理异常)
Unusual database activity
Presence of malware or other files
Signs of DDoS attacks
Typically, however, they are specific MD5 hashes of malware, IP addresses, or URLs of domain names or botnets
Tactics, Techniques and Procedures
Tactics, Techniques and Procedures (TTPs) are descriptions of the behaviours of threat actors.
Tactics are the high-level overall objective of an attacker split into phases of the kill-chain.
Techniques are the next level down and describe the general behaviour to achieve the tactical objective
Procedures are specific instances of behaviour to carry out a technique using particular software
TTPs are thought to be specific to particular threat actor groups because of the Pyramid of Pain:
Attribution (归因)
Attribution to a particular threat actor group is supposed to help because:
It reveals motivations and objectives of the attackers and so can potentially help in stopping progression of an attack
Helps understand the impact of the attack e.g. crime vs espionage (间谍)
MITRE ATT&CK framework is based entirely on this premise. Contains information about 110 different groups and hundreds of TTPs.
Problems with this when you look at the actual distribution and uniqueness of the TTPs however
Attribution is a very difficult topic as it is so open to False Flags (假旗,即攻击者伪装成其他攻击者) and geopolitical posturing (地缘政治作秀行为)
Incident Containment (遏制) Eradication (清理) & Recovery (恢复)
The first challenge is containment to stop further impact. This may involve:
Disabling accounts
Blocking network traffic
Isolating a computer or segment of the network
Balance the strategy against (遏制的时候需要权衡):
Potential damage to and theft of resources
Need for evidence preservation
Service availability
Time and resources needed
Effectiveness of the strategy
Duration
Alerting the attackers
Malware may detect attempts to disable and then take actions based on that.
Eradication and recovery may involve rebuilding computers or recovering from backups.
Must ensure that all malware is removed.
Update accounts.
Incident Post-Incident Activity
Lessons learned
Breach notification to appropriate authorities
Notification of affected users and follow-up
Reputation management
Insurance claims
Analysis of incident data