CPU
· The CPU processes instructions and data that are stored in memory.
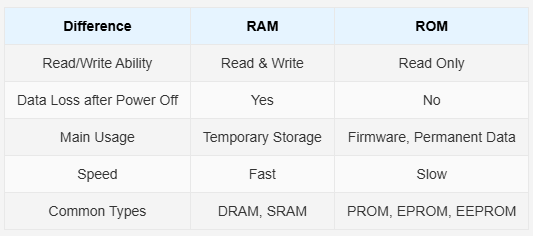
· Memory is either random access memory (RAM) or read only memory (ROM).
· Instructions and data are transported between memory and CPU over a Bus.

· CPU can also read/write data from I/O device.
· Instructions processed by CPU are simple operations like ADD, SUBTRACT, AND, OR, XOR, etc.
Booting Up
· When a computer is powered on, the firmware in ROM is loaded and run. This is the BIOS (Basic Input Ouput System).
· The BIOS will run a Power-On Self Test (POST) to check for hardwares like display/keyboard/network card/memory etc.
· The BIOS will then load the first 512 bytes from the hard drive called the Master Boot Record (MBR). This contains the bootloader code that will execute and load the OS.
Operating System
· The operating system is responsible for a number of different tasks
Running and scheduling applications to run and share resources such as CPU, Disk, RAM.
Allows for memory virtualization.
Controlling access to I/O devices through I/O Driver software.
Manage access control and authentication.
Handle communication via networks.
Handles graphical user interfaces.
· Kernel
CPU operates in different modes: User Mode / Supervisor Mode.
Applications are run in different protective rings organised from most priviledged Ring 0 to application level code Ring 4.

Applications that are scheduled to run are prioritised depending on which ring they run in.
Ring 0 only allows trusted code to run there.
File System
· File
A named collection of information stored on a storage device such as internal disk or external USB drive.
Has metadata like name/type/location/size/protection/creator/creation time etc.
Has an owner and permissions for access control.
· Organised in directories or folders.
· OS supports a file system which is a way of organising files on a disk, providing operations of creating/reading/writing/deleting files.
· Devices can be logically viewed as files too.
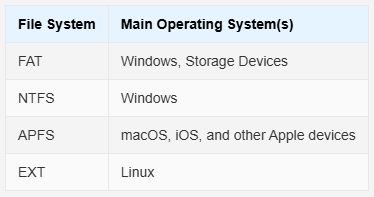
· Numerous file system types: FAT, NTFS, APFS, EXT etc.
· Access is controlled by discretionary and role-based access control.
Processes
· The operating system is responsible for running programs and managing their access to system resources.
· When a program is running it is known as a process and multiple processes may be running at the same time.
· The process may be in a number of different states depending on what actions it is performing or whether it has used up its time quantum.
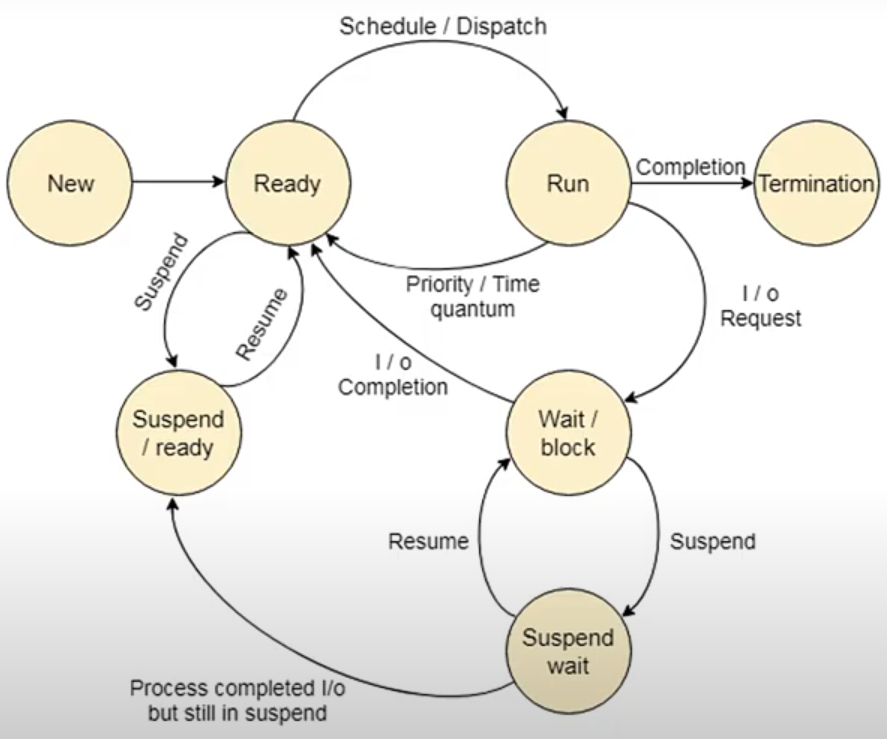
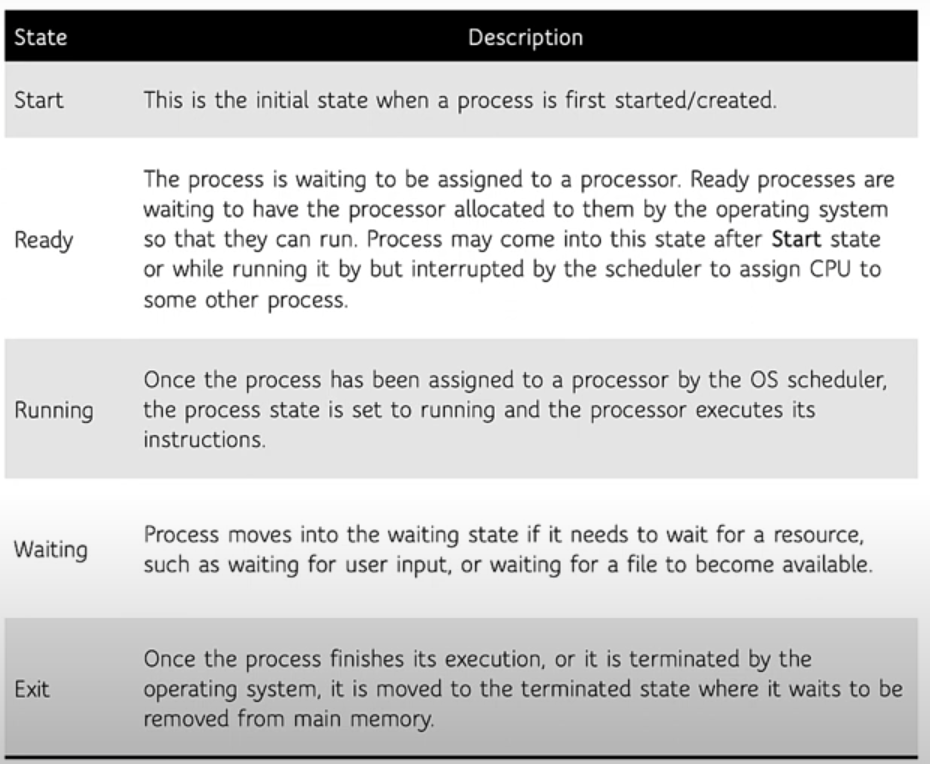
NOTE: Suspend state is also known as Sleep state.
· Processes are scheduled by the operating system according to one of a number of different algorithms.
· Processes may run at the same time if the computer has multiple processors.
· Simultaneous execution can happen through multithreading. (Also tech called hyper-threading)
· Attributes of process
Process ID (pid): A process is uniquely identified by a numeric identifier.
Parent: All processes are started by another process and so maintains links to their parent and may inherit attributes such as open files and access to terminals. Parent processes are identified by the Process Parent ID (ppid).
Files: Processes work on files (and devices that are represented as files) and so information about these are kept for each process.
Virtual Memory: A process is allocated memory to store the code and data that it operates on. If this becomes too large for physical memory, it may be mapped to disk.
Access Control
· Access control restricts who has access to an object (e.g. file) and what operations they may perform on it.
Discretionary Access Control (DAC)
Mandatory Access Control (MAC)
Role-Based Access Control (RBAC)
Rule-Based Access Control
Attribute Based Access Control
· Discretionary Access Control (DAC): Each object has an owner who grants access to other users.
· Role-Based Access Control (RBAC): Access is granted by administrators to groups of users based on their roles.
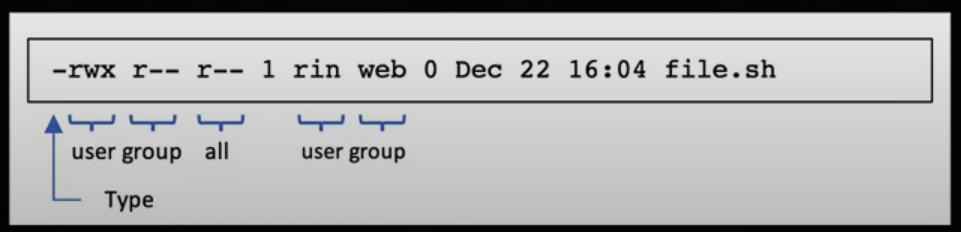
· Linux and Windows file systems use this two to achieve access control.
· In Linux, r (read), w (write), x (execute), are set on each file/directory.
· Rule-Based Access Control: Access based on rules/policies. For example, Firewalls.
· Attribute Based Access Control (ABAC): Access granted on attributes (device/location/time etc). For example, WiFi restrict access based on MAC address.
· Mandatory Access Control (MAC): Access is granted based on labels assigned to the user and the object.
IP Addresses
· In the Internet layer, TCP/IP uses IP addresses to identify the machine that is sending, and the machine that is going to receive the packet. The IP address is normally 4 numbers separated by full stops.
· To make it easier to find addresses, we can use a domain name.
· TCP/IP uses a Domain Name Server (DNS) as a directory to do the translation. The DNS is a service that internet service providers (ISPs) and organisations run to manage their own domain names.
HTTPS/TLS
· HTTPS is a secure version of HTTP that initially used SSL (Secure Socket Layer) although this became TLS (Transport Layer Security).
· Current version of TLS is 1.3 although 1.2 is still prevalent.
· TLS makes use of certificates that havethe verified identity of the server and the server's public key.
· The certificate is verified by a trusted certificate authority. Browsers maintain a list of these that gets updated from time to time.
TLS 1.3
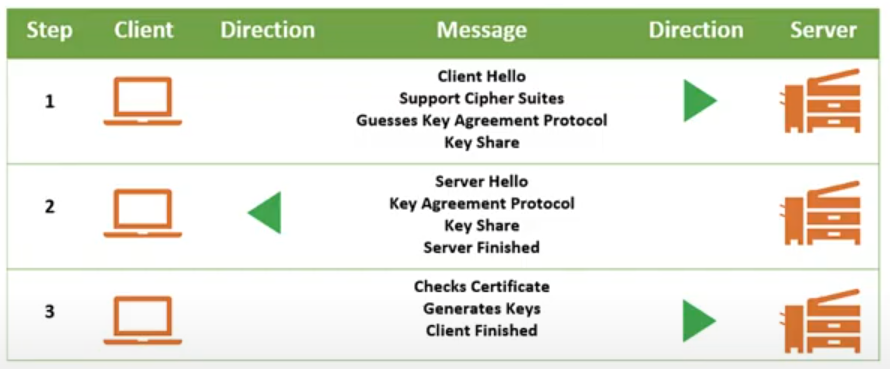
· TLS estabilishes a connection by exchanging messages to:
Agree the cipher that will be used.
Which key exchange protocol to use.
Create and share keys
Check server and client identity through certificates.
VPN
· Virtual Private Network (VPN) software allows a computer on one network to create a direct connection to another network over a secure link.
· Effectively you get an IP address on the network you have connected to.
· VPNs can run over a number of different protocols: e.g. IPSec, OpenVPN, IKEv2 and WireGuard.
· Communications are encrypted and so not visible to anyone inspecting traffic - even to the ISP you are using.
· Connecting to a network in a different country will make it appear that the computer is in that country, but location can leak from other sources such as the browser.
· VPNs provide security through encrypted communication and privacy through the VPN provider not keeping logs.
· VPNs do not provide anonymity.
Tor and The Dark Web
· Tor (The onion routing project) is software that provides IP anonymity by bouncing encrypted packets over a set of Tor servers called relays or nodes.
· How Tor Works:
The Tor client obtains a set of nodes from a directory server.
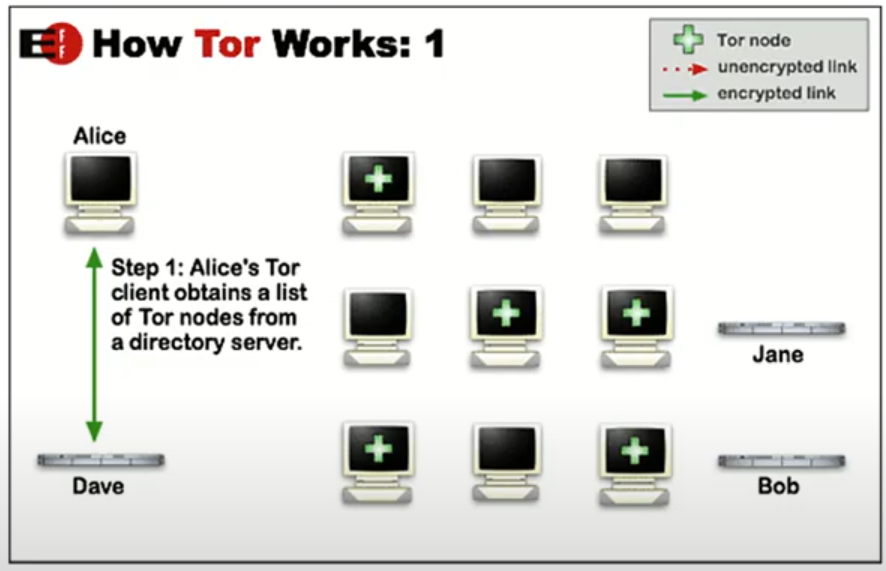
The Tor client decides on a random path through the nodes and encrypts the message with each node key.
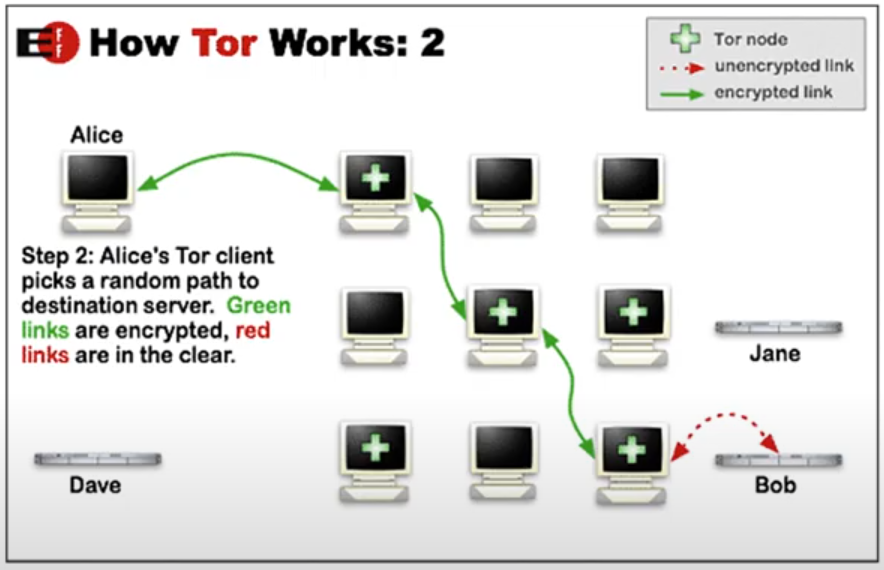
· Tor uses an address called an onion address to connect to services offered on the Tor network, these address are like URLs.
· The Dark Web is essentially the collection of onion services that are not indexed directly by search engines on the "regular" web.
· Because of the anonymity provided by Tor and the semi-hidden nature of onion services, many illegal activities have flourished with Dark Markets selling illegal products that are paid for using cryptocurrencies.
· The anonymity provided by Tor is also of more positive use by activists and those simply wanting to browse the web anonymously.
